The Nihilist OPSEC Blog I
The Nihilist OPSEC Blog was originally published on nowhere.moe. In May of 2025 it went darkweb only and in June of 2025 it went offline. It is being preserved here.
Editor's Note: Not long after I published this article, the blog went back online so I've updated the links and probably will not continue this series unless the blog goes down again. There's a lot of resources on this blog so please check it out.
Defining Concepts With Analogy
Privacy, Anonymity, and Plausible Deniability
Here in this case, we can say that the conversation between Bob and Alice is private, because it excludes Jack from spying on the conversation.
Here in this case, we can say that the person talking to Alice is Anonymous from Jack's perspective, until he can figure out who he really is. Until that someone makes an OPSEC Mistake (such as saying out loud his real name, or where he lives), he remains Anonymous.
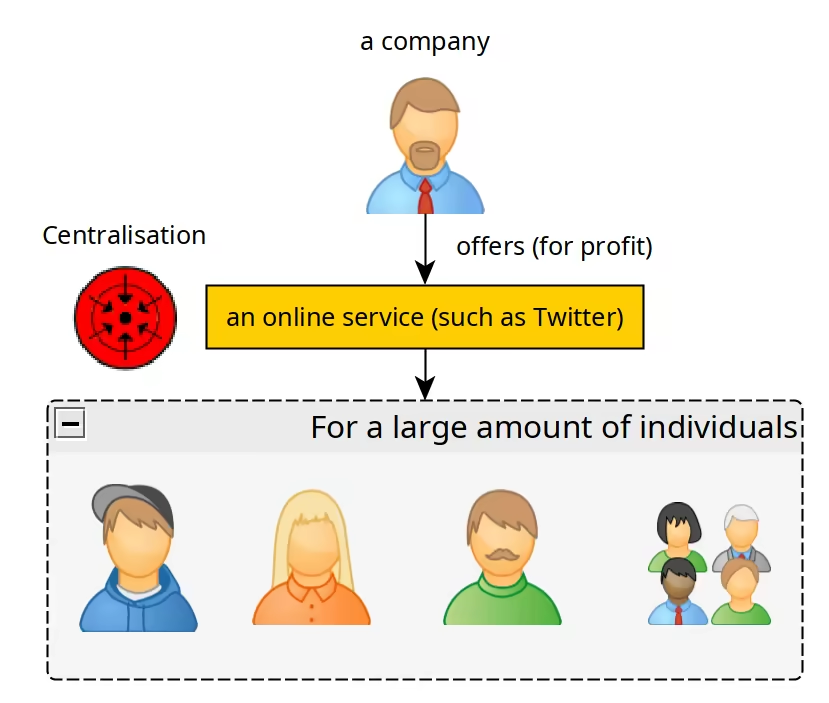
Centralisation, Federation, and Decentralisation
Here, a profit Company offers an online service (such as Twitter) for their own profit, most often they will do everything they can to keep as many users on their service, in order to gather as much personal information about them as they can, for their own profit.
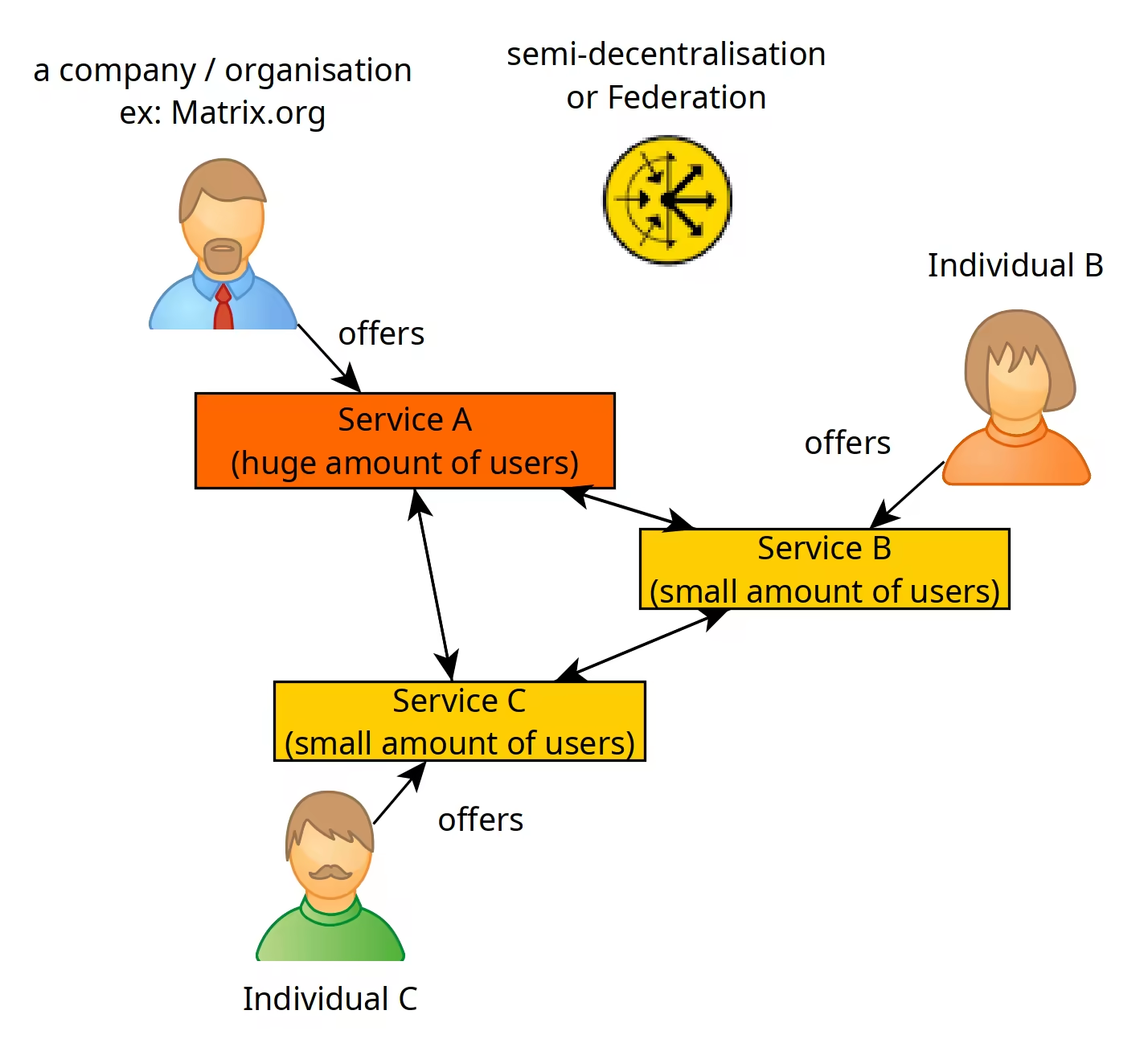
A federated service can be considered as semi-decentralised, due to having a company running the main instance that contains a huge amount of users, while other instances can be ran by individuals with a smaller amount of users. The federation means that instances connect to each other so that individual B may talk to individual A, or individual C.
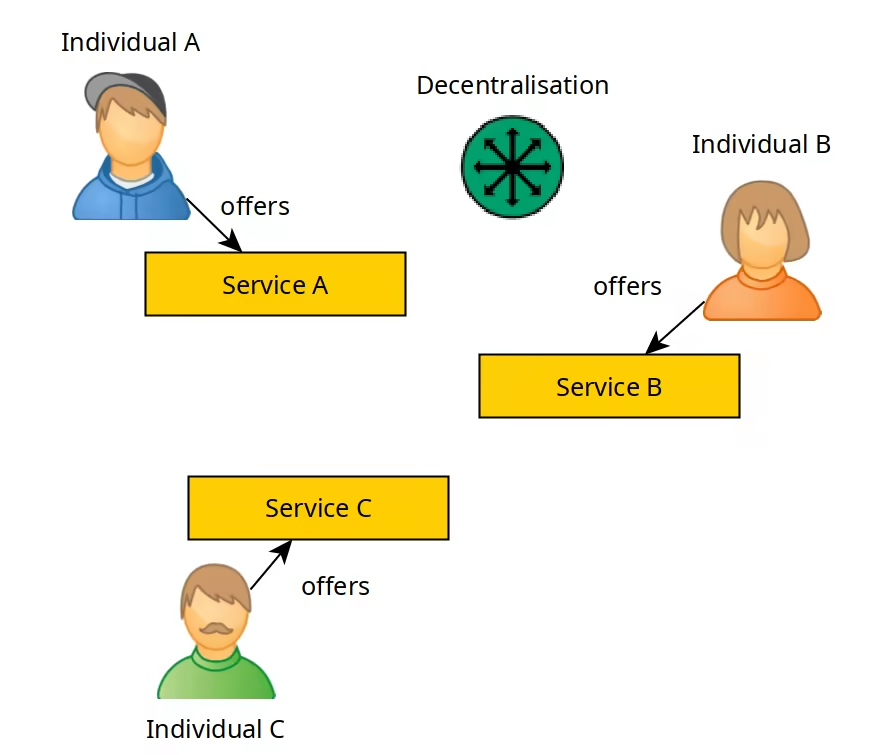
We can say that a service is decentralised when individuals are running the services themselves, and offering them back to the individuals, without any profit company coming into the picture.
Security and 0days
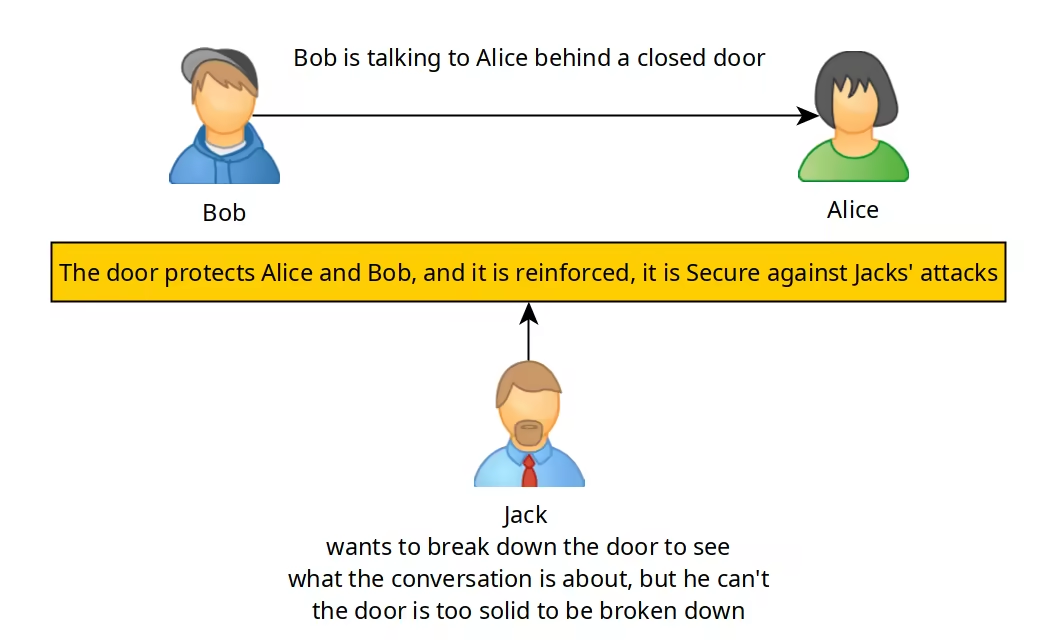
Here in this case, we can say that the door is secure because it protects Alice and Bob's conversation from Jack's attempts to hear the contents of the conversation.
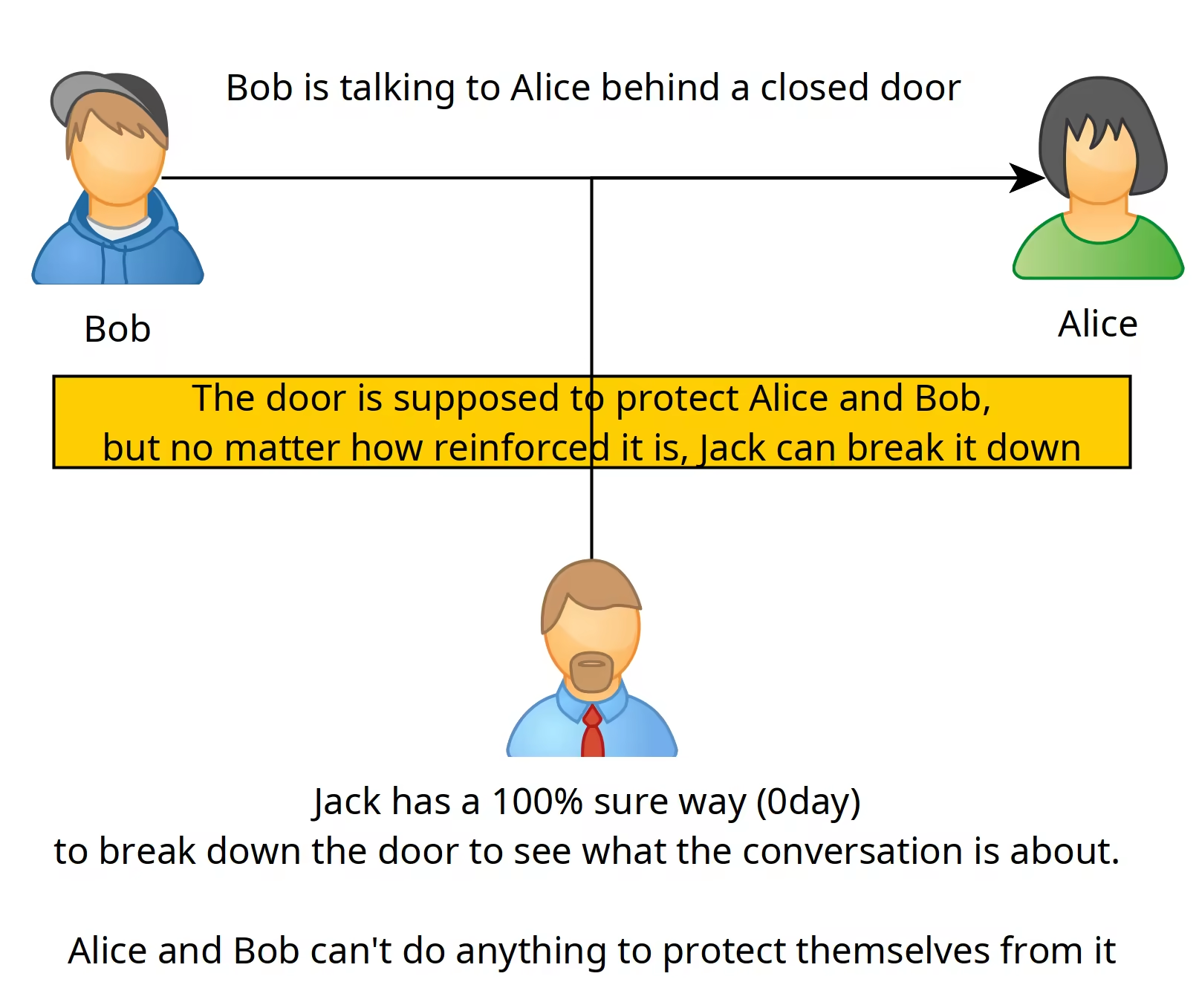
Bob and Alice are supposed to have their conversation protected by a closed door, but Jack has an 100% sure way of breaking down the door, no matter how they try to reinforce the door, There is nothing Bob and Alice can do about it.
Governments and Centralisation
A government is the system or group of people governing an organized community, generally a state.
Their primary focus is to maintain their control over the country/state, no matter the cost, they will do everything possible to remain in power for as long as possible
They are the ones who write the rules, the laws by which everyone in the country must must follow for society to remain in order (wheter the subjected people accept it or not), according to them.
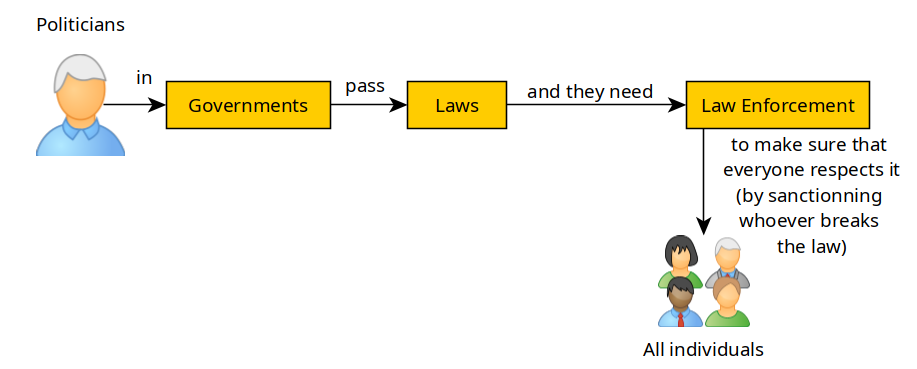
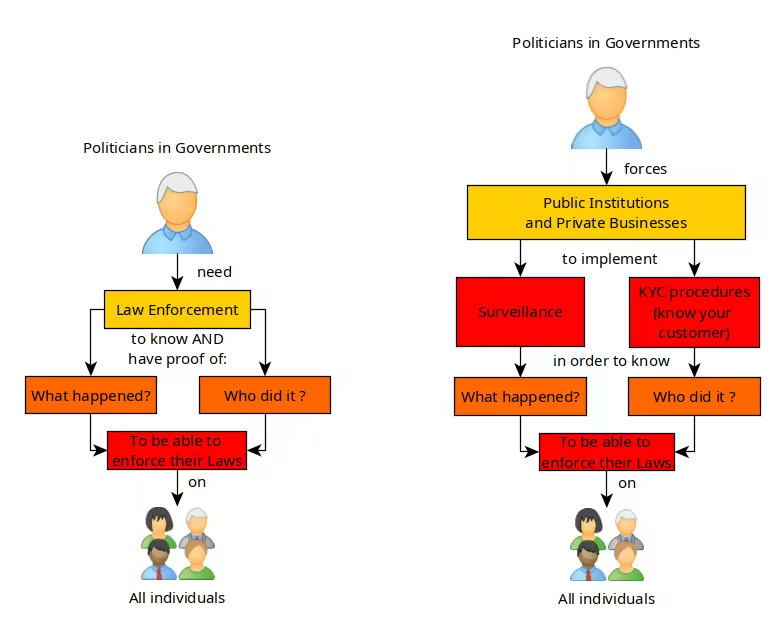
Governments pass Laws and to make sure that their laws is respected, they need Law enforcement (LE) to be able to apply sanctions on whoever breaks their laws.
Governments nowadays almost always use bogus reasons to use to pass abusive laws (the typical "it's to fight the boogeymen!" type of reasons) , in order to either make more money, or to enforce surveillance better, or to straight up take away power from businesses and individuals.
Businesses and Centralisation
One thing that governments genuinely care about is how modern and economically mature their country is. Hence their close relationships with businesses that generate the most wealth in their country.
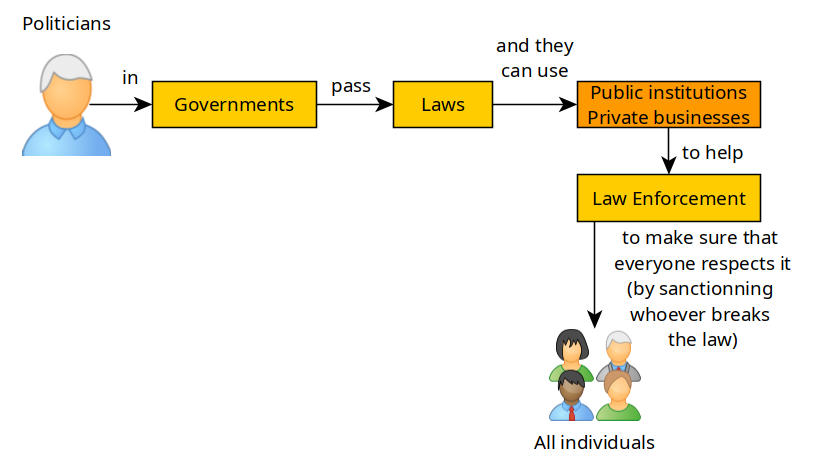
These same businesses are often a tool of Centralisation, to extend the government's reach of power, the most common trait there is surveillance, and identifying who did what (ex: with KYC procedures).
Each business is closely regulated, the bigger the business, the higher up the priority list it is to be audited for regulation compliance checks. The exception being with International Banks (ex: see the HSBC scandal) due to everyone's innate greed to get richer even if it means breaking the law.
Businesses are centralised entities just like governments, they ALL can act as proxies to help law enforcement, wheter they want to or not.
Law Enforcement
Law enforcement is the activity of some members of government who act in an organized manner to enforce the law by discovering, deterring, rehabilitating, or punishing people who violate the rules and norms governing that society.
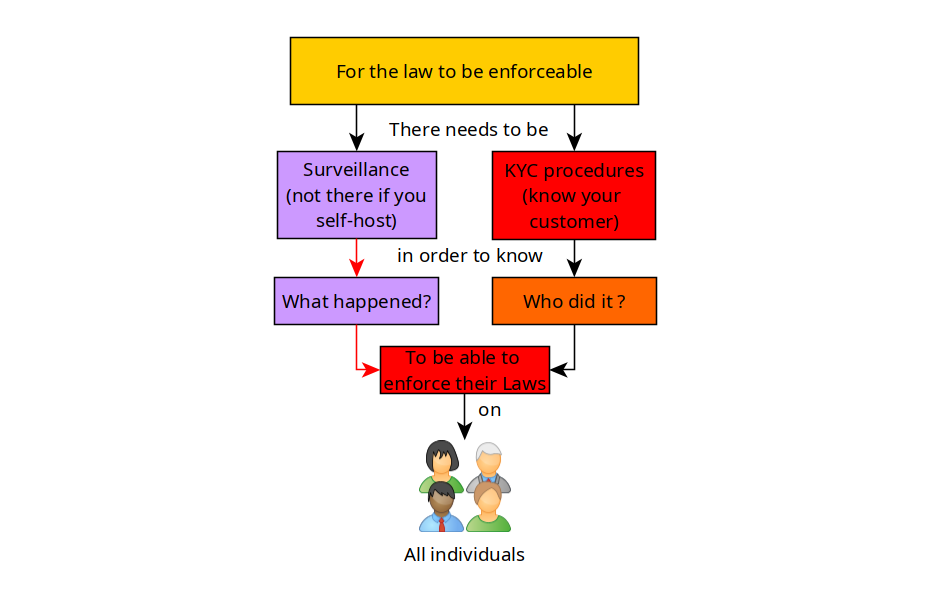
For the Law to be enforceable the authorities need to know 2 things:
- What happened? (lack of Privacy)
- Who did it? (lack of Anonymity)
Of course, the law must not be ignored by anyone, and to make sure that everyone is kept in line, they need to show everyone that the law is effectively enforced onto those that behaved badly, very often they brag about catching criminals to let everyone know that they are the good guys protecting everyone from the bad guys.
That is the basis of this whole Privacy and Anonymity talk. In short, For the law to be enforceable, they need to know both what happened, and who perpetrated the act to be able to apply sanctions on the individual / group of individuals that committed the crime.
Modern governments know this very well, and some go to extreme lengths to make sure that every citizen is under surveillance.
A very common practice for Law enforcement is also to either bribe or force legitimate businesses to give the data they possess of their users, to know if a crime has been commited or not. See the USA's recent FISA 702, good news is they're not lying about it anymore, the intention is clear and out in the open. The general idea is that this bill is meant for the government to be able to force anyone (individual or business) to conduct spying activities for the governments, with or without their consent, with a gag order.
In short, the US government grants itself the right to force you or your business to do anything to further their agenda. This world's biggest democracies are all turning into dictatorships in the name of national security.
Anyway you get the idea. Anonymity is more relevant than ever, we're headed for that surveillance dystopia China has currently established.
Governments and Decentralisation
As we have discussed previously, governments love centralisation. It's an easy way for them to extend their power to directly affect users of said centralised businesses. Take for example how the US government uses banks to impose financial sanctions onto whoever they consider as a threat to them.
They have largely succeeded in keeping their population hooked onto centralisation, for example you want to watch videos you think youtube, you want to browse the web you think google, social - facebook, twitter, and so on. It's become a natural reflex for most people, hence most people flock to these centralised platforms, and as we have explained previously; governments use them as proxies to spy or enforce censorship onto it's citizens.
It's convenient for them; you own a large service, which attracts millions of people to use it, and so governments would love to have access to that data you own, to be able to know what's happening. (remember FISA 702)
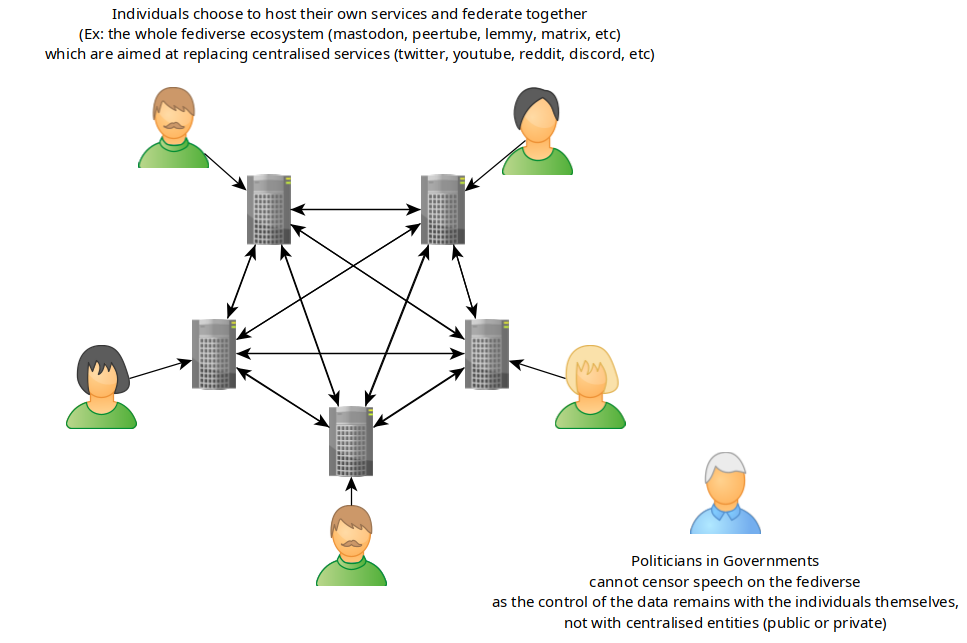
If the masses were to completely change their habits and embrace decentralisation, like i am trying to promote on nowhere.moe for example using peertube to replace youtube, matrix to replace discord, mastodon to replace twitter, etc, it would seriously limit the reach of the power they try to have on the population. They wouldn't be able to censor and try to control the public opinion of the people like they did through twitter for example.
The key difference here is that the INDIVIDUALS are the ones controlling the service, and they're making the overall decentralised ecosystem grow larger and larger as they keep federating together.
So in this case, you are taking out the first pillar that is required for law enforcement ; Surveillance , the government would have to knock on your door, and FORCE you to give them the data of your users (which they have done by the way; see kolektiva.social).
I encourage everyone that's fed up with the arbitrary administration of centralised services to start using their decentralised alternatives, see what the Fediverse has to offer for more details.
Governments and Anonymity
That's an easy one. as we discussed, for the law to be respected, it needs to be feared by the population, to make sure it remains feared, it needs to be enforced by authorities (law enforcement or LE for short). To do so they need to know what happened, and they need to know who did what.
That's why they go to such extreme lengths to implement surveillance wherever they can. (see China's surveillance state, the USA's FISA 702, and the EU trying to pass anti encryption laws)
Anonymity is a great thing to look for if you care about privacy. It's the perfect way to know if a service intends to respect your privacy or not.
The reason being, that if you use a service anonymously, you are taking out the other pillar that is required for the law to be enforceable, making sure that they cannot know it was you who used the service.
The Anonymity Test
If you want to know if a service intends to respect your privacy or not, access it, and use it anonymously. (use the Tor browser to access it, and see if it accepts monero as payments). Check out my tutorial on OPSEC (Operational Security) to understand the full reasoning.
You will see that you can already rule out Google, youtube, twitter, instagram, snapchat, Facebook, Baidu, Whatsapp, etc. All of those services sell the data they collect about you to each other, including to governments (see the cambridge analytica scandal)
Stop using services that treat you as a product to sell, regain your lost dignity and defend it.
EDITOR'S NOTE: For brevity, some sections that contain more "why does the author write about OPSEC" than "how can the reader implement OPSEC" have been omitted. You can find these entries in full at archive.org
What Is Privacy?
In short, Privacy means that you are not under surveillance. In this example, Bob wants to talk to Alice privately, so he shuts the door on the prying eyes of Jack. So that he can't hear their conversation.
Privacy is Bob and Alice's ability to seclude themselves from the awareness of others. It is the ability that Bob has, to close the door on Jack, so that he cannot see his actions anymore.
When you are looking for Privacy, always ask yourself : Privacy from what? Privacy from whom? in other words, Who do i want to close the curtain on?
Privacy and Surveillance
In this current world we live in, Surveillance is nearly omnipresent, where there is a business involved, and especially closed-source software, Surveillance is right there.
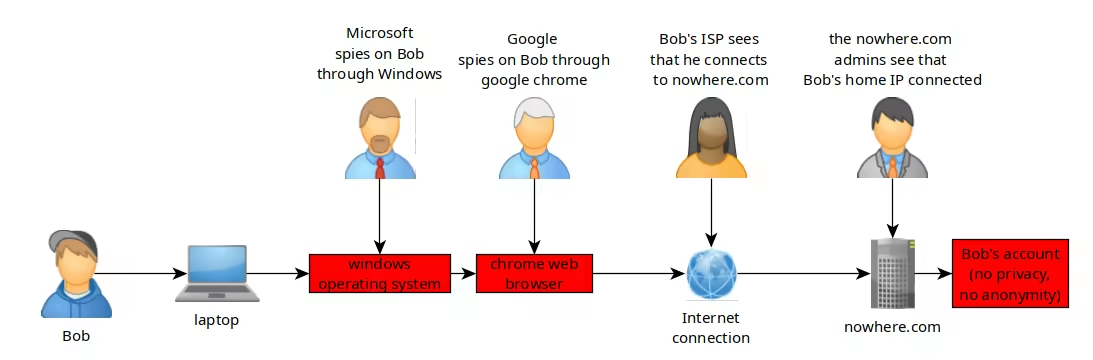
Here's an example where Bob (which represents nearly 99% of the people out there) is being spied on by:
- Microsoft (because Bob uses Windows)
- Google (because he uses Google and Google Chrome)
- Bob's ISP (because he doesn't use a VPN nor Tor)
Editors Note: What if we wanted privacy from the VPN company? What if we wanted privacy from the TOR exit node?
If Bob were to do something sketchy using his computer, Law Enforcement would obtain all the information they need to know what Bob did, because he used Windows, Google Chrome, and no VPN/Anonymization network.
And it does not stop there, even when LE is not involved, politicians can also request and pay to get private user data , at the discretion of those large companies that specialize on infringing upon users' privacy for their own profit (see the cambridge analytica scandal).
Your personal data is being sold by large corporations, for their own profit, and your consent is of no concern to them.
The Panopticon
The Panopticon originally was a prison building design, which was designed by the social theorist Jeremy Bentham in the 18th century, where the core concept revolved around making all prisoners to be observed by a single cop, without the inmates being able to know whether or not they are being watched.
The idea is that every inmate, since they don't know whether or not they are being watched, they would have to assume that they were under constant surveillance, forcing all of them to behave at their best, even if the cop is not looking in their direction.
Now you probably get where i'm trying to go with this, this is the narrative that governments are trying to push, that everyone's actions are under constant surveillance, that everyone must behave at their best at all times if they don't want to end up in jail. And how convenient it must be for those governments, they have the vast majority of their populations giving away their privacy in the name of convenience by using closed-source software on their phones, on their computers, on their laptops, on their routers, etc.
If privacy doesn't matter, i hope you won't mind me installing a camera in your bedroom, filming you 24/7 right?
Ask yourself this simple question: "Who should be aware of what I do?"
Let's take the most common example you can encounter: "Should a company (such as Microsoft) be able to spy on what I do with my computer?"
How many people are we talking about exactly? How big is Microsoft Corporation? How many of them can see what you do with your computer?
In other words, are you ok with having an entire crowd being aware of your actions?
You better be a good speaker if that is the intent, remain aware that you are stepping up on a stage for many people to see what you are doing, when using closed-source software.
Is that normal to you? Do you like putting your every action on display for everyone to see?
If your answer to that question is no, Then it's time for you to close the curtains, so that this crowd can't see anymore. To close the curtain, you need to stop using closed-source software.
Closed Source Software
"Hey, I just wrote this code, I compiled it, it gave me this .exe file, run it on your computer! What? You want the source code? Hell no, just trust me bro!" Or in other words, why can't I trust an adversary to not look at me when I install one of his cameras in my bedroom?
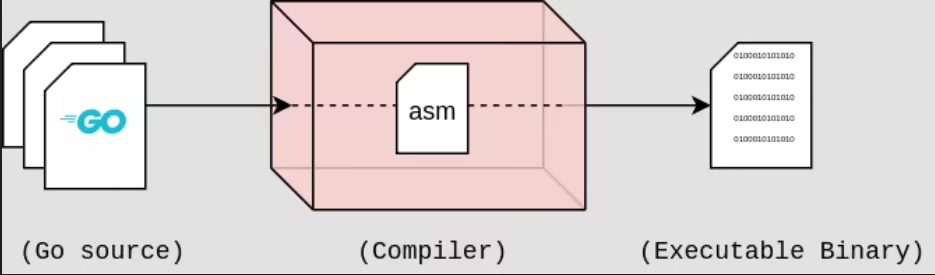
To briefly explain, any software out there was first written (a developer wrote some source code, for example in the Go language), it was then compiled, and then the compilation produced a binary file (for example it became a .exe file on windows)
The catch here is that when you try to reverse-engineer binary files, it's going to be very hard to figure out what the original source code was. This practice is called Reverse Engineering, a niche in cybersecurity, where someone tries to figure out what the original sourcecode was intended to be, with only the binary to work with.
One thing is for sure: you can't arrive at the original sourcecode from just the binary. It's mostly guess work.
Most software companies (which can be corporations) out there are greedy, they work hard to produce software, and they hate to have any competition. Hence they want keep their software sourcecode private, to make it as hard as possible to others to arrive at the same level of functionality. That is exactly why closed source software is used by most people.
The most popular example out there is Windows, they would definitely not like their sourcecode to be leaked/reversed like it with Apple's IOS.
Privacy Is not a Spectrum
Like we have explained previously, privacy is binary, you are either being watched, or you are not being watched.
Whoever tries to tell you that "Privacy is a spectrum" are just trying to justify that you should leave at least some closed source software on your computer if you don't feel like it, in the name of convenience.
No you should not, you either have privacy or you don't. You definitely do not have privacy when there are 100 cameras from 100 different adversaries in your bedroom, and it is the same thing as with leaving ONE camera from ONE adversary in your bedroom , the simple fact remains, you do not have privacy as long as there is a camera pointed at you.
When you have Windows installed, you constantly have a 100 cameras pointed at you, no matter what you do on the OS.
When you have MacOS installed you may have 70 cameras pointed at you, you don't have privacy there all the same.
You may have linux installed with only FOSS software, except that you have installed one closed-source software such as Discord, meaning you have only one camera pointed at you, and because of that one closed-source software you didn't remove yet, you don't have privacy either.
So when you go on communities online that pretend to talk about privacy, you need to remain vigilant to what they recommend you should do, If at any point in time it includes doing something on Windows or macOS or using any other closed-source software to have privacy, you need to realize that they are trying to mislead you into a false sense of privacy as shown in the examples above.
Why is this relevant for Privacy?
Privacy as a usecase on your computer requires that you only run software from which you are able to read the sourcecode of:
I can just as easily write a software (let's say a chat application like Telegram), I can make that software grab as much information as possible like save the computer model, serial number, get information on what other apps are running on your computer, what's the public IP address, take screenshots of what you're doing on your computer, and I can make that application send all of that sensitive information to a remote server, while officially pretend that the additional network traffic is for "for telemetry purposes".
All i need is to simply prevent you from being able to read the sourcecode, that way you have no way to disprove that this isn't actually telemetry.
What's happening is that you have no visibility on what the software is doing, it is not transparent.
Once that's in check, you should spend some time to read the sourcecode of the software you are running. Or at the very least listen to what other privacy-minded people have to say about each piece of software. So that you are able to know that the software does not contain any spying mechanism.
If you find any software that actually does telemetry or any other spying mechanism, you should remove it from your computer, if you intend to have privacy there.
It is only once you destroy all the cameras in your bedroom, and once you close all the blinds that the adversary outside can't peek into what you're doing in your bedroom. In the same way, closed-source software is exactly the same, a camera for an adversary (the manufacturer of that software, or the government that they act on behalf of) to peek into what you're doing on your computer.
Keep that in mind, as this is the ABC of OPSEC you'll have to remember throughout the rest of the next blogposts i write, On any device of yours, there is only one type of acceptable software for Privacy, and that is FOSS software. It has always been this way, and will always remain this way.
If at any point in time you see people recommend closed-source software for privacy purposes, you need to realize that they are either misled or are actively trying to mislead you into a false sense of security, and you should remind them that privacy and closed-source software are mutually exclusive. hence the non-negotiable need of using FOSS software for privacy.
Security in FOSS
Open Source Software is essential for security.
A common argument made for closed source software is that it is 'more secure', often brought up in disagreements like iPhone vs Android or the general Company Software vs Community FOSS debate.
In reality, security is compromised and reduced when software is closed source.
We have to first understand that perfect security is not possible. There will always be potential vulnerabilities in any software regardless of what it is. This what security patches and updates are for, changing of the software to fix issues.
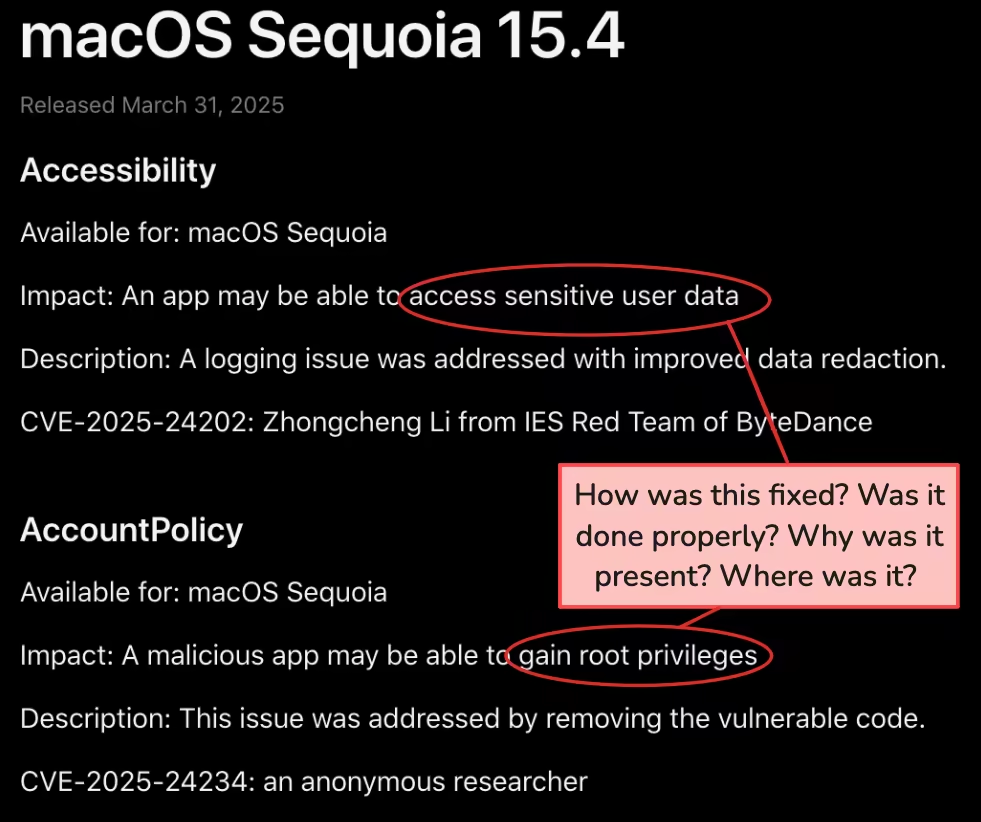
Let's compare Apple's MacOS vs the Linux Kernel as an example to display why open source is better for security. Below is an image of the top section of of Apple's security page for MacOS Sequoia 15.4.
Although we get brief confirmation that the listed vulnerability has been fixed, we cannot actually verify the patch. We have to trust that it has been fixed reliably in the MacOS source code and none of the questions listed above are answerable.
This opens up several questions or even threat vectors. If the patch was not done properly and created a new vulnerability, we would not be able to tell. Or if a malicious government/adversary pressured them into adding a backdoor or spyware into a patch, we similarly would have no way of knowing. Put simply, nearly all specifics of updates are opaque and only known to the developers.
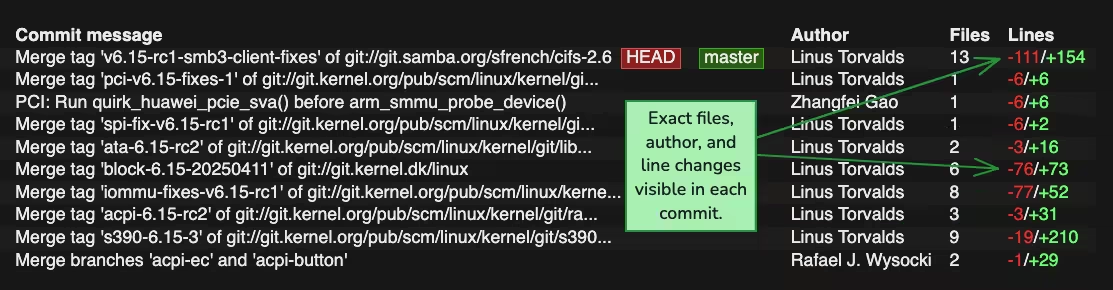
Below is an image of the Linux kernel's git history.
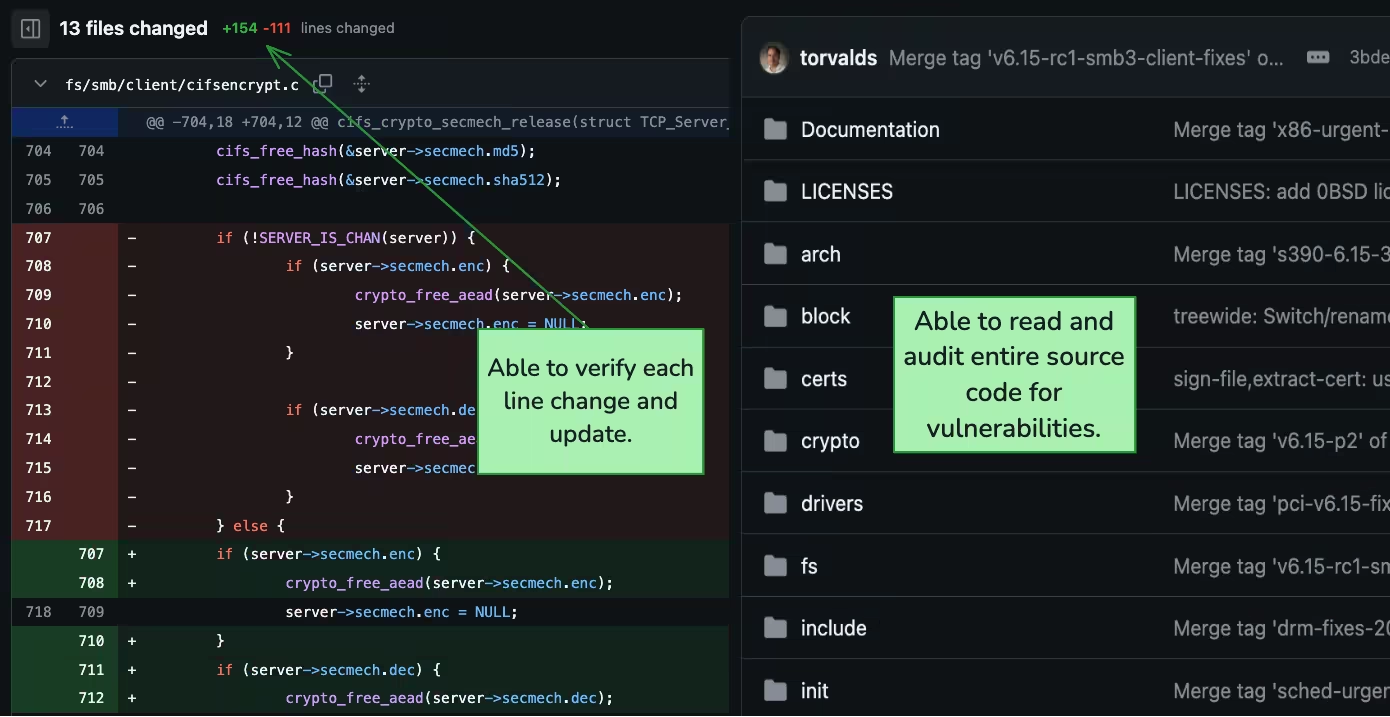
Unlike the one sentence security patches on the MacOS page, you can see every single line of code that was changed in each commit of the Linux kernel. This transparency and visibility is very important for security.
Firstly, unlike only the Apple developers being able to patch security vulnerabilities or review the source code, anyone can review the source code of the Linux kernel. This means that vulnerabilities can be searched for in the source code itself instead of just on the application layer. The concept of security through obscurity or purposefully making software closed is flawed since that does not actually solve existing vulnerabilities.
Having source visible almost always leads to high security since anyone can submit patches after their code review if they found an issue. Compared to just a single developer team for the closed source software, the number of eyes on the code of a piece of open source software is much higher, which means more code review and more safety testing, ultimately leading to greater security.
Editors Note: Not all FOSS software is used by enough people such that it has many eyes or more safety testing; in these cases, open source software does not benefit from what is described above.
Moreover, the visibility is crucial: Apple can claim they fixed a critical security issue but as mentioned, we cannot review the code ourselves to check if it properly fixes it or of there is spyware/a backdoor. In open source software, we can verify the update and make sure there isn't any spyware ourselves.
The transparency and availability in open source software provides auditable, trustable changes and the best possible security.
Spyware by Example
Discord: a Privacy Nightmare
Let's take a popular example: Discord as detailed in their article on spyware watchdog, it's one of the worst pieces of spyware out there. It's sourcecode is not public, and they confirm that they collect large amounts of sensitive user data (as much as they can).
Discord even goes out of it's way and contains a process logger to spy on what you do on your computer.
That service even forces you to add a phone number in case if it suspects you tried to create an account anonymously (via a vpn or via tor).
You get it, it's a nightmare for privacy and anonymity there is out of the question. The perfect governmental proxy to spy on the masses.
SimpleX : The Decentralised and Open Source Alternative
Take the counter example, SimpleX is an open source chat application.
Meaning if there were any spyware to be baked into the software, you would see it in the sourcecode, and rest assured the entire open source community would go into huge turmoil to blame the developers and you would know it.
Remove surveillance using FOSS
To conclude, here are the requirements you need to look for, for any software that you use:
- It must be FULLY free and open source (FOSS)
- Ideally, if servers are involved, it must be self-hostable (for decentralisation) (meaning the serverside code must also be fully open-source -- see how this is no longer the case with Signal)
- It must implement privacy features like encryption.
- It should not contain any telemetry, or any spyware.
- It should ONLY do what it was originally meant to do.
By that standard, you can already discard software like Windows, Discord, Whatsapp, Instagram, iOS, pre-installed phone host OSes, Word, Excel, etc, as none of them are open source, and you can be damn sure that they are spying on everything you do, willfully or not. (ever since the US government passed the FISA section 702.)
YOU CAN NEVER TRUST PEOPLE. SO YOU CAN'T TRUST THEIR CLOSED SOURCE SOFTWARE. YOU CAN ONLY TRUST TECHNOLOGY THAT CAN BE VERIFIED! SO YOU NEED TO USE OPEN SOURCE SOFTWARE FOR PRIVACY USE CASES!
Now that you have the full reasoning laid out, and if being watched by an entire crowd when you are using your computer doesn't sit well with you, it's time for you to move out of all that surveillance, out of that theater/circus that is closed-source software (in which you are the clown on stage, for corporations to see), it's time for you to close the blinds and declare that the show is over to these entire crowds that have infringed upon your basic right of privacy. It's time to install Linux.